
Emotet, a powerful piece of malware that has infected computers of individuals and businesses throughout the world, was disrupted this week by law enforcement agencies that seized both the servers controlling it as well as people suspected of keeping it running.
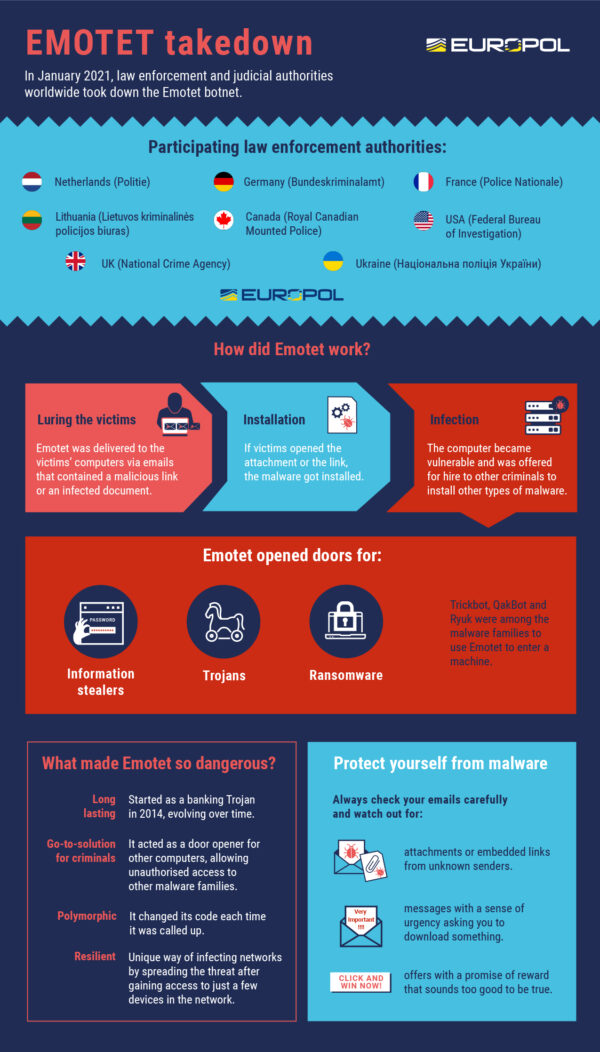
In one of the most significant takedowns of malware operations in years, authorities from the Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada and Ukraine worked together to shut down computers that control the malware.
Law enforcement and judicial authorities gained control of the infrastructure and took it down from the inside this week, according to Europol.
“The infected machines of victims have been redirected towards this law enforcement-controlled infrastructure,” the regional law enforcement agency stated in an announcement today.
Emotet is notorious for being a “door opener” for a number of cyber attacks that can be executed after hackers gain access to a victim’s computers. They can install ransomware or steal sensitive information, for example.
Typically, Emotet works by tricking a user into opening an e-mail attachment, disguised as an invoice or resume, for example, and unwittingly creating a backdoor to his computer.
This access is then sold “as a service” to other cyber criminals who want easy way to mount a cyber attack in future.
First conceived as a trojan for stealing banking credentials in 2014, Emotet is remarkable in how it has morphed over the years. As it spreads, it changes its code slightly to avoid detection by cyber defences.
In 2019, Singapore cybersecurity firm Ensign said that the malware had been detected in half of the machines it had scanned in the country. Emotet was found in the manufacturing, financial services, media, aviation and healthcare sectors here.
Elsewhere, Emotet’s attacks have been well documented. In 2019, the Berlin Court of Appeal and the University of Giessen were both hit by it, according to cyber security firm Kasperksy.
Today, Dutch authorities who took control of two Emotet command and control servers are said to have pushed an update to automatically uninstall the malware on victims’ computers on March 25, reported ZDNet.
It added that Ukrainian police have announced the arrest of two individuals believed to be tasked with keeping Emotet’s servers up and running (video below).
How effective will this takedown be in keeping Emotet-wielding cyber criminals off the Internet? It depends on how widely their networks have been disrupted, say experts.
Threat actors rebuild their botnets following other takedown or disruption efforts, although the likelihood of this scenario hinges on the significance of the individuals who have been apprehended, said Kimberly Goody, senior manager of cybercrime analysis for Mandiant Threat Intelligence.
“Notably, the actors behind Emotet have existing partnerships with other notable malware operations, including Trickbot, Qakbot, and Silentnight,” she noted.
“In addition to distributing these families as secondary payloads, we have occasionally observed Emotet being distributed by these families in the past,” she added. “These existing partnerships and renewed spamming could be leveraged to rebuild the botnet.”






