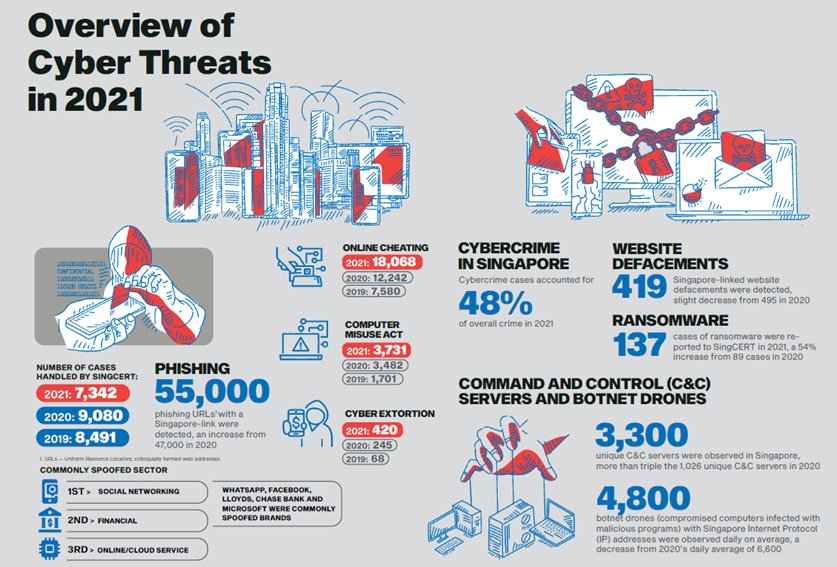
A growing number of ransomware attacks continued to menace Singapore businesses while cybercrime cases, especially online scams, were a top concern in 2021, reported the Cyber Security Agency of Singapore (CSA) today.
Last year, 137 ransomware cases were reported to the government agency, up 54 per cent from 89 cases in 2020. The cases affected mostly small-and-medium enterprises (SMEs) from sectors such as manufacturing and IT.
The around-the-clock nature of these sectors’ operations meant there was less time to patch their systems, thus potentially allowing ransomware groups to exploit vulnerabilities, according to the CSA.
It observed that ransomware groups targeting SMEs in Singapore utilised the Ransomware-as-a-Service (RaaS) model, which made it easier for amateur hackers to use existing infrastructure – created by developers – to distribute ransomware payloads.
As for cybercrime, there were 22,219 cybercrime cases in 2021, a 38 per cent increase from the 16,117 cases in 2020.
Online scams were the top cybercrime in Singapore, accounting for 81 per cent of cases. A separate 17 per cent were Computer Misuse Act offences and 2 per cent were cyber extortion cases.
Singapore was not just a target for hackers but also a place where they launched attacks from. Given the country’s good digital connectivity and trusted reputation, this was no surprise.
There were 55,000 unique Singapore-hosted phishing Web addresses (with a “.sg” domain) in 2021, up 17 per cent from 2020, according to CSA.
Social networking firms made up more than half of the spoofed targets, according to CSA. Malicious actors’ were likely exploiting public interest in WhatsApp’s updated privacy policy announcement on users’ phone numbers being shared with Facebook.
Of course, hackers never let a crisis go to waste, either. Scammers also exploited the Covid-19 pandemic amid the Omicron sub-variant outbreak in late 2021 to spoof government websites, according to CSA.
In 2021, there were also more malicious command-and-control (C&C) servers hosted in Singapore that were used to distribute malware and take control of victims’ computers.
There were 3,300 such C&C servers last year, more than triple the 1,026 in 2020, according to CSA. This was the largest number recorded since 2017.
This spike was driven by a large increase in servers distributing CobaltStrike malware, which made up nearly 30 per cent of all C&C servers observed, according to CSA.
On new trends and concerns, the agency warned that crypto-based crime has been increasing. Borderless and distributed platforms, along with anonymity features, have made it difficult to track illicit activity and enforce regulations across borders. Criminals are emboldened, as a result.
Another worrisome trend is hackers targeting critical Internet of Things (IoT) devices, such as connected Uninterruptible Power Supply (UPS) units, which could lead to significant downtime.
IoT devices often lack critical cybersecurity protection, CSA warned. Employees have also been known to connect their personal IoT devices to an organisation’s networks without the knowledge of security teams, it noted.
Over the years, the government has tried to get businesses and end-users to be more proactive in keeping out cyber threats. For example, CSA has worked with the Infocomm Media Development Authority (IMDA) to offer SMEs pre-approved cybersecurity solutions.
Since 2017, more than 6,000 SMEs have benefited from these cybersecurity solutions that provide endpoint protection, managed detection, response and unified threat management. Clearly, more needs to be done to combat the growing threat.
“The cyber landscape in 2021 was fraught with increasingly sophisticated threats and more brazen threat actors,” said David Koh, the commissioner of cybersecurity and chief executive of CSA.
Calling cybersecurity a team sport, he added: “Governments, businesses and individuals must continue to do their part to strengthen our collective cybersecurity posture.”